4 Practical Steps to Strengthen Your OT Cybersecurity Program
Do you manage industrial equipment, smart building systems, or even a simple warehouse conveyor belt? If so, you rely on operational technology (OT) e
READ MOREScam in CS2 – What Is It and How to Avoid It
The CS2 (Counter-Strike 2) skin market is a multi-billion-dollar ecosystem with millions of players buying, selling, and trading in-game items every d
READ MOREERP Software for Industry-Specific Needs: What to Consider?
The worldwide ERP software market valued at $54.76 billion in 2022 continues to expand at an 11% compound annual growth rate during the forecast perio
READ MOREWork-From-Home Scams: Common Signs and How to Protect Yourself
These days, work from home is at an all-time high. It's much more convenient than working from the office, as it doesn't require waking up early, comm
READ MORE✅ From Invisible to Irresistible: Upgrade Your Cyber Resume and LinkedIn
Top Cybersecurity Tips Every College Student Needs in 2026
In 2026, college life is more connected than ever—classes, assignments, finances, and social life all run through your devices. But this convenience c
READ MORECybersecurity for Teachers – What Educators Need to Know in 2026
👨👩👧 How to Talk to Your Kids About Cybersecurity (Even If You’re Not Tech-Savvy)
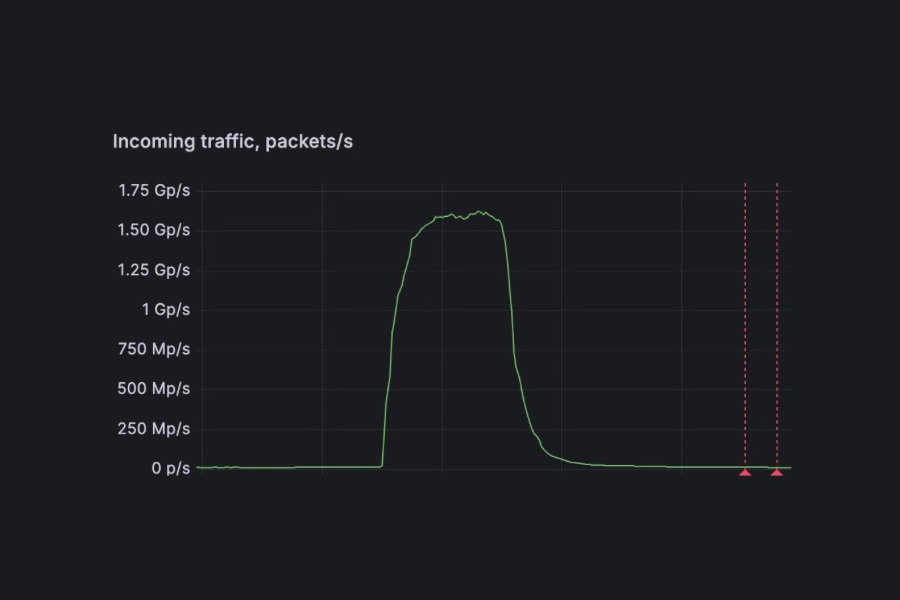
1.5 billion packets per second DDoS attack detected with FastNetMon
London, United Kingdom, September 11th, 2025, CyberNewsWire FastNetMon today announced that it detected a record-scale distributed
READ MOREHow Advanced Gaming Tools Like ESP and Aimbots Are Shaping Competitive Play
Competitive gaming has grown from basement LAN parties to a multibillion-dollar global industry. Esports tournaments now fill arenas, attract sponsors
READ MORECTEM or Breach: Living with Exposure in 2026
Cyber threats are evolving faster than businesses can patch up and secure their systems. The traditional security approach, which involves annual pene
READ MOREWhy Cybersecurity Leaders Are Turning to Device Intelligence to Tackle Digital Threats
Across industries, digital transformation has created new opportunities for growth. Banks, insurers, fintech platforms, retailers, and online marketpl
READ MORE